
As indicated in the previous post for the Insights into MEF’s SD-WAN Standard blog series, the past year has seen the industry’s first SD-WAN standard (MEF 70) gain significant momentum. Many of the largest Managed Service Providers (MSPs), including AT&T, Comcast Business, PCCW Global, and Verizon among others, and their vendors — VMware VeloCloud, Fortinet, Nuage Networks, Versa Networks — have become MEF 3.0 SD-WAN Certified.
Now that the MEF SD-WAN standard is on track towards a major upgrade in 2021, attention in the MEF community has shifted towards one of the most significant industry challenges — enhancing network security. As reported in the Futuriom SD-WAN Managed Services survey and depicted in Figure 1, improving network security is the most important factor for enterprises considering SD-WAN managed services versus the Do it Yourself (DIY) model.
As COVID-19 accelerated the migration of applications and data to the cloud and the Work from Home (WFH) trend, the Secure Access Service Edge (SASE) architecture emerged. Originally introduced by Gartner in 2019, the distributed SASE security architecture claimed to address the issues faced by a global remote workforce and overcome the limitations of the traditional physical security perimeter.
Throughout 2020 the pandemic raged and SASE products and services began to proliferate. However, the lack of a common definition and standardization resulted in a free-for-all. Vendors and service providers began rebranding their offerings as SASE — so-called “SASE-Washing” — to address the demand.
Market proliferation and ensuing confusion motivated the MEF Board of Directors to assess the evolving security requirements. Most of the directors were experiencing rapid shifts in their own organizations path towards digital transformation, including increased reliance on the cloud.
Consequently, MEF launched a series of investigations, soliciting inputs from the MEF community. As with the SD-WAN standard, MEF surveyed early market entrants to ensure that real-world experience and actual SASE products were considered in future standardization.
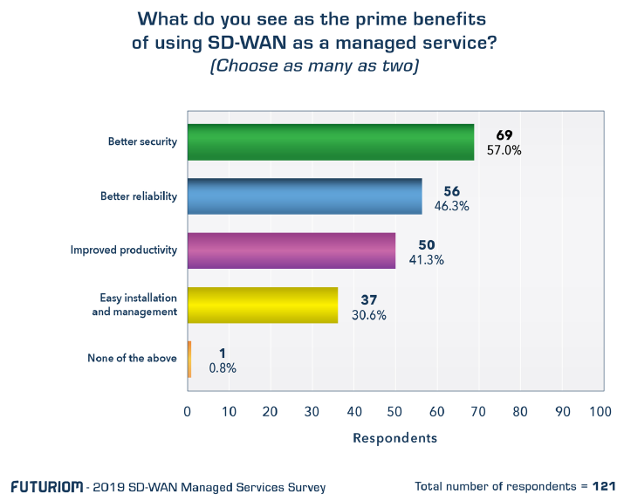
Figure 1: Security is among the top benefits of using SD-WAN managed services
Source: Futuriom – 2019 SD-WAN Managed Services Survey
Standardizing Network Security
Since its inception in 2001, MEF has standardized telecommunications technologies for the world’s most prominent service providers, solution providers, and technology innovators. MEF standards originated in Layer 2 (Carrier Ethernet) — from which the organization was named. As the internet rapidly evolved, MEF moved up the stack to Layer 3 (IP), NFV, and SD-WAN.
Network security is complex, posing new standardization challenges as we move to the top of the stack, and the cybersecurity market is highly segmented (see Figure 2). Therefore, Standards Development Organizations (SDOs) must adequately scope the problem statement.

Figure 2: CyberSecurity is a highly segmented market
Source: Foundation Capital
As Andrew Tannenbaum observed in his classic text Computer Networks, “The nice thing about standards is that you have so many to choose from.” To be relevant, standards must be timely, extensible, practical, and attract a sufficient following to justify the new work.
MEF standards:
- Assert common terminology and acronyms that span the family of standards.
- Standardize a framework (which enables services to be instantiated) versus a service (a single instance).
- Define and specify a service interface between a Service Subscriber/Buyer and Provider/Seller.
- Assume a black Box between the Service Subscriber and Provider and typically do not govern the implementation.
- Specify the Service Attributes — common information agreed to by both parties.
- Allow options to be as inclusive as feasible to the vendor community.
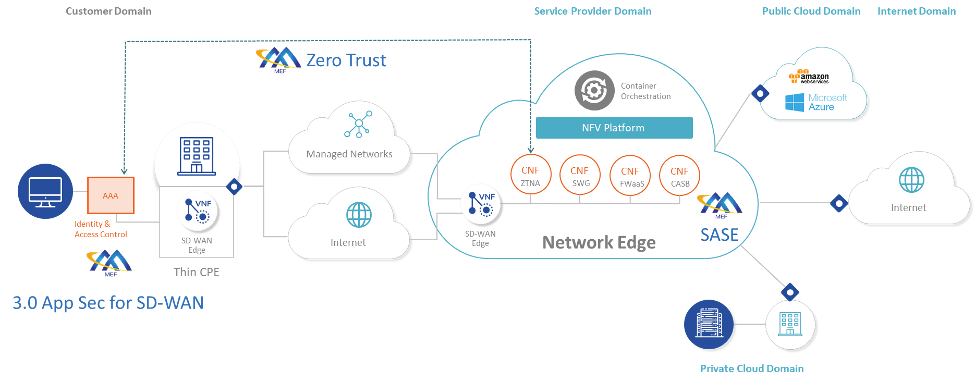
Figure 3: MEF security architecture for the multi-cloud environment
Source: MEF
MEF’s initial foray into security standardization was built upon the success of the SD-WAN standard. In 2019, MEF initiated the Application Security for SD-WAN project (MEF 88), which specifies a set of security functions for protecting SD-WAN managed services. For additional details, refer to Part Three of this blog series and MEF 88 (in Draft Standard and expected to be ratified in 2021).
Upon concluding its investigation in 2020, MEF embraced the SASE architecture and introduced a pair of new security projects to address the changing landscape: SASE Service Definition (MEF 117) and Zero Trust Framework (MEF 118).
Figure 3 depicts the resultant MEF security reference architecture, illustrating the relationship between the three security projects:
- MEF 88 Application Security for SD-WAN defines security functions commonly applied to the SD-WAN environment.
- MEF 117 SASE Service Definition specifies a SASE-based, distributed security service where (MEF 88) security functions migrate from the data center and CPE to edge clouds.
- MEF 118 Zero Trust Framework specifies a dynamic means of continuously assessing access to cloud-hosted applications and data using a Zero Trust model.
The MEF security architecture enables MSPs, Managed Security Service Providers (MSSPs), and their vendors and Systems Integrators (SIs) an opportunity to leverage their SD-WAN customer relationships into new revenue opportunities.
The reference architecture offloads security functions from the customer premise and moves them to edge clouds operated by the MSP/MSSP. End users access cloud-hosted services on a variety of public, private and hybrid clouds via SD-WAN. These run over a variety of WAN connections, including highly scalable direct internet connectivity.
Multi-cloud access is governed by SASE-based policies and each access request will be authenticated by leveraging the Zero Trust Network Access (ZTNA) paradigm. This requires application- and user- identity management and policy-based access control evaluated by context. This provides a robust means of implementing a highly distributed service with globally dispersed users.
MEF security architecture benefits:
- The cloud native approach is highly efficient to implement, scale and maintain.
- Cloud Security Functions (CSFs) protect employees and corporate resources wherever they are in the world. Non-cloud-hosted security functions can also be utilized.
- Access to the network is granted based on user and application identity and context.
- Access controls are dynamically enforced for each access attempt based on identity, time of day, role, and other enterprise policies.
- Management is logically centralized and decoupled from the underlying infrastructure.
While the MEF 88 is currently a draft standard, MEF 117 (SASE Service Definition) and MEF 118 (Zero Trust Framework) are just getting underway.
In an upcoming post, we will delve into the details of MEF 117 and MEF 118, as the MEF pursues the first SASE and ZTNA standard.
Other posts in the “Insights into MEF’s SD-WAN Standard” series:
- Part One: Overview (July 31, 2019)
- Part Two: Technical Approach (August 14, 2019)
- Part Three: Application Security Project (January 14, 2020)
- Part Four: MEF SD-WAN Certification Program (March 23, 2020)
- Part Five: MEF SD-WAN Certification Turns 1: Lessons Learned from the Industry’s First SD-WAN Standard (Feb 1, 2021)
